Enable Cloud Security with Proveho Networks
Value Proposition
Develop Cloud Security Risk Management Framework Aligned with Organisational Objectives
Provision Security Architecture across Disparate Computing Domains
Enable Security Program and Processes Consistent with Acceptable Risk
Continual Security Assurance across Software Development Life-cycle
The Value of Cloud Computing
Cloud computing is transforming the way technology services are delivered and consumed, driving business efficiency and disruptive innovation, thus emphasizing the need for cloud security.
The Agility and Economics of Cloud Services are Indisputable.
Proveho Networks assists Organisations in Developing and Maintaining Secure Cloud Computing Practices consistent with their Objectives and Risk Appetite.
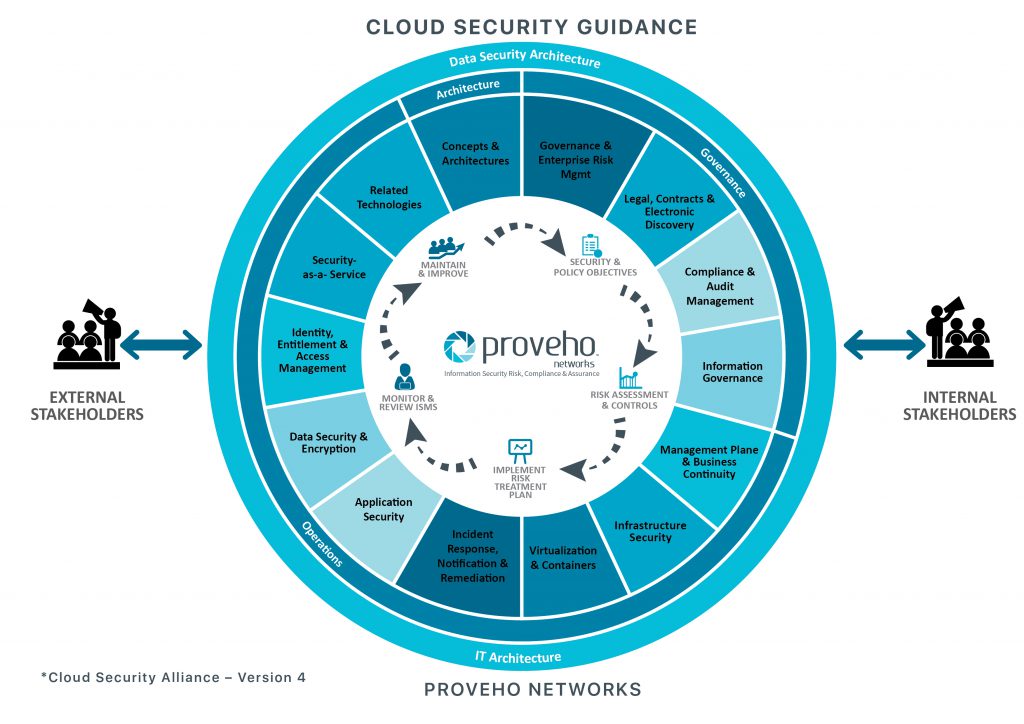
Insufficient risk modelling, inadequate cloud security and complexity of cloud services may increase the operational risk exposure. Organisations are confronted with an increasingly fragmented computing domain and surging mobile-device to user ratio that further expands cloud complexities.
Constant software development and integration program, along with deeper visibility and access into the enterprise’s operational systems, dictates security assurance processes are embedded in the software development life-cycle and applied to monolithic software and emerging micro-service architectures alike.
Managing security risk and compliance requires the development of security program complementary to and consistent with Cloud Service Providers obligations for underlying cloud infrastructure, whereby the organisation has no access. Inherited cloud provider security compliance documents, collated with complementary organisational security practices, are critical to managing security and compliance risk.
Protecting information is more involved in a cloud environment. Managing the information security life-cycle around how data is captured, processed, archived, and destroyed across heterogeneous cloud service models is critical to maintaining an acceptable information security risk profile. Managing access control across the information life-cycle is fundamental security assurance requirement.
Responding to time sensitive security incidents and conducting forensics analysis in a restrictive multi-tenant cloud environment requires planning and instrumentation of cloud computing environment for monitoring and detection of anomalies and commensurate incident response.
Secure Cloud Computing Engineering Services
Proveho Networks assist organisations to develop and implement an identity and access management (IAM) architecture that provides secure federated user access to critical cloud services.
Proveho Networks develops and implements encryption architecture that is aligned with organisational security requirements, digital roadmap and across fragmented computing domains.
Proveho Networks is aligned with industry bodies and leading application security vendors to develop software application security architecture and security testing throughout the software life-cycle.
Proveho Networks leverages leading solutions from Cloud Security Access Brokers vendors to manage the movement and security of profiled data onto and within authorised cloud platforms.
Proveho Networks leverages Defence-in-Depth principle for cloud computing environment aligning with reputable vendors and integrating the relevant best practices to provide security assurance.
Proveho’s Security Incident Management capability assists organisations in monitoring, detecting, and responding to security incidents across computing domains during and after the fact.



