Secure Digital
Transformation with
Proveho Networks
Value Proposition
Cyber Security Risk Management Aligned with Organisational Priorities & Strategy
Cyber Security Risk profile Consistent with Acceptable Risk Limits & Compliance Obligations
Cyber Security Risk Managed Across People, Process & Technology
Investment in Cyber Security Initiatives Enable Secure Digital Transformation
Value in Managing Cyber Security Risk
What is our risk exposure? How secure are we? How much security is adequate? Are we compliant? How do we know when our security objectives are achieved?
Proveho Networks assists organisations to address such questions.
Capturing organisational context is fundamental to optimising return on security investment.
Proveho Networks Assists Organisations in Developing and Maintaining Security Practices Consistent with their Objectives and Acceptable Risk Limits.
Insufficient risk modelling, inadequate security and complexity of digital infrastructure may increase the risk to operational mission critical tasks. Organisations are confronted with an increasingly fragmented computing domain and a surging mobile-device to user ratio that further expands security assurance requirements.
Consistent software development model, along with deeper visibility and access into the enterprise’s operational systems, dictates security assurance processes are embedded in the software development life-cycle and applied to emerging micro-service and monolithic software architectures alike.
Demonstrating compliance requires producing artifacts across fragmented computing domains. Inherited cloud provider security compliance documents collated with complementary organisational security practices are critical requirements to managing shared security tasks as well as compliance risk.
Protecting data is more involved in a cloud environment. Managing data security life-cycle around how data captured, processed, archived, and destroyed across all cloud services models – including access control – are critical for developing and maintaining an acceptable data risk profile.
Responding to time sensitive security incidents and conducting forensics analysis across restrictive computing environment requires systematic planning, instrumentation and monitoring across computing domains for detection of anomalies and commensurate security incident response.
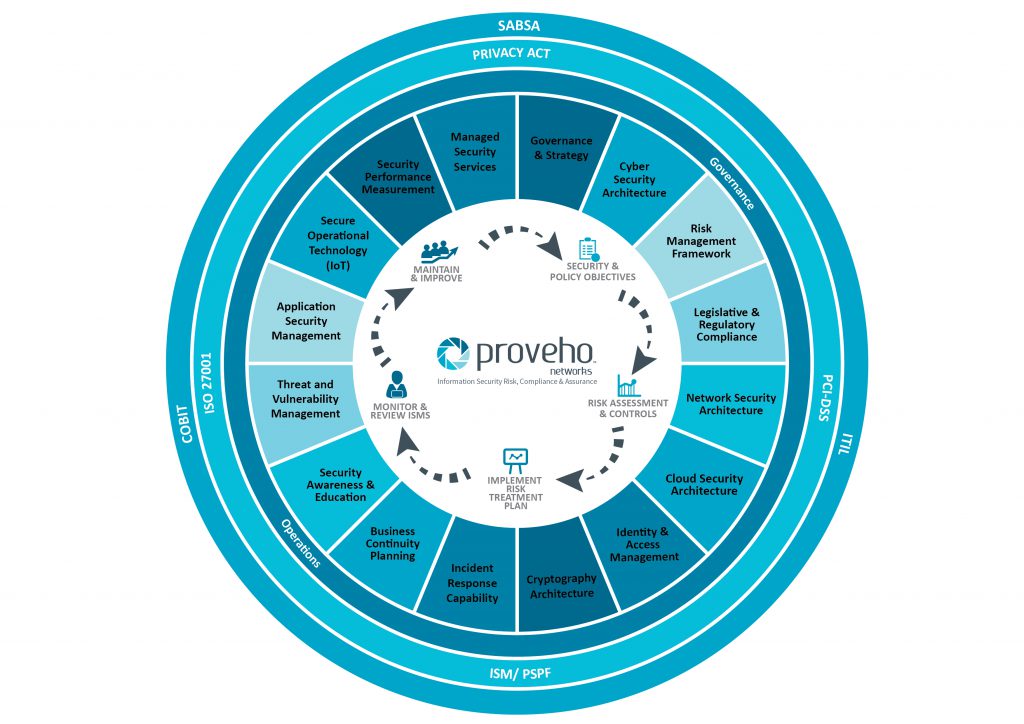
Proveho Networks Information Security Engineering Services
Capturing and modelling of organisational operational and strategic context is critical in enabling business transformation and aligning cyber-security risk management to support business objectives and strategy.
Contextual business security attributes are not limited to just criticality and sensitivity of data but extended to include adjacent attributes such as usability, extensibility, and compliance requirements.
Proveho Networks provides application security assurance, aligned with industry bodies and leading application security vendors, to develop software application security architecture model for organisations.
Proveho Networks security risk consultancy practice and security engineering services assist organisations with managing security risk with existing technology infrastructure and securely planning for and adapting to new business models.
Proveho Networks brings a wealth of knowledge and security experience across diverse industries including global supply chain, financial institutions, government, technology supply chain and startups.
Proveho Networks provides Incident Response Capability that is critical to managing, detecting, and responding to security incidents across fragmented computing domains during and after the fact.



