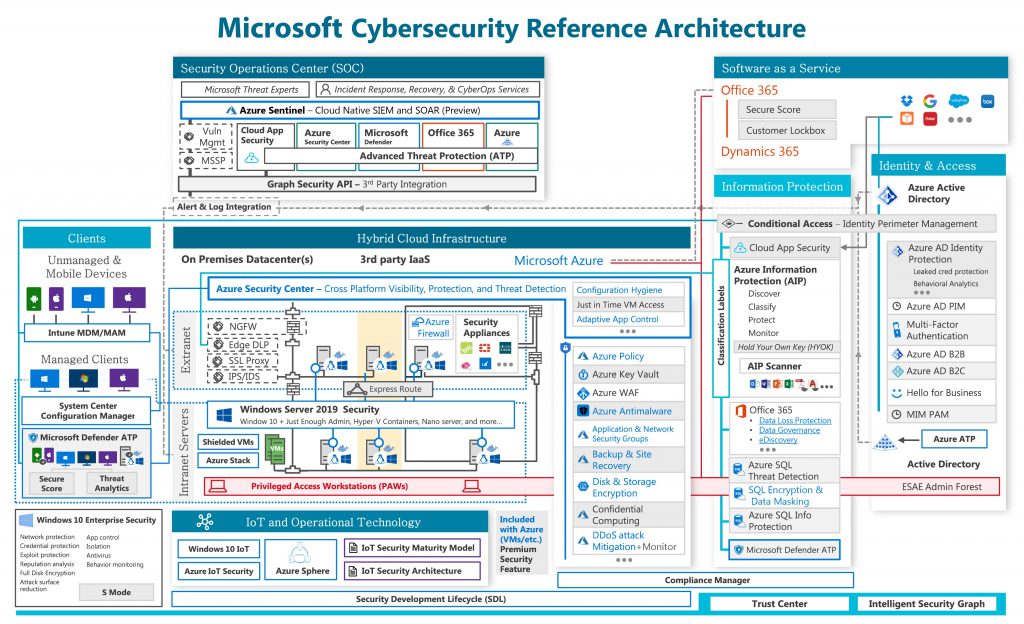
Can the cloud vendor be trusted with an encryption methodology, including the keys encrypting your data? While providing convenience of centralized user management, federated user identities often grant excessive privileges with limited or no visibility to the connecting endpoint device’s risk profile and location. Responding to time sensitive security incidents and conducting forensics analysis in a restrictive multi-tenant cloud environment requires planning and instrumentation of a cloud computing environment, with a secure encryption architecture, for monitoring and detection of anomalies.
Data encryption to manage data governance in cloud environment requires an encryption framework that is consistent with the cloud computing footprint and services, compatible with the identity and access management repository and inter-operable with relevant security controls external to the cloud domain. Proveho Networks develops and implements such architecture that is aligned to organisational requirements, roadmaps and acceptable risk limits.