The Value of SOC
The increased frequency, diversity and magnitude of cyber security threats pose unanticipated risks to organisations, who now require additional capabilities to detect and appropriately respond to such threats to minimise adverse effects. Thus, managed SOC service is necessary for those organisations
Incident response is predicated on security capability. The global connectiveness of digital assets, anonymity offered by the internet and increasing complexity of modern computing architecture, allows attackers to launch incursions freely.
Proveho’s approach to managed SOC architecture and service enablement is provided. Understanding an organisation’s key operational objectives, capturing baseline behaviour, developing incident categorisation and escalation criteria, and defining key threat detection use-cases and are some of the many critical success factors for SOC service.
Security threat intelligence. Establishing an inventory of digital assets and associated vulnerability profiles, mapping security controls overlay, and capturing generated events in a normalised format from heterogonous platforms across diverse computing environments form the foundational elements of SOC. These are critical to achieving network visibility and behaviour.
Proveho Networks ensures SOC Services are fit for Existing and Future Environments.
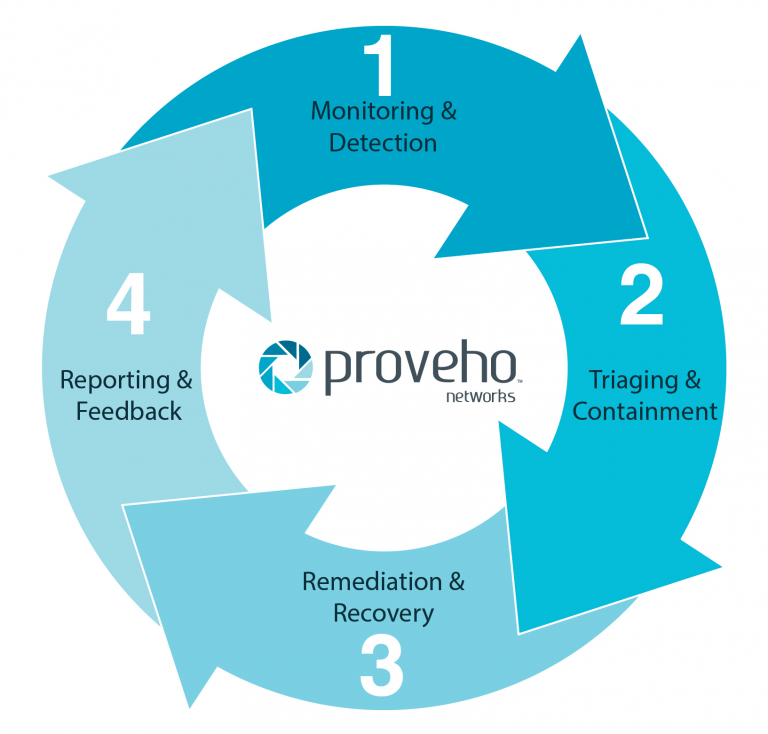
Advanced analytics will reduce incident investigation cycle times. Looking ahead, maturation of advanced automation and sophisticated security analytics models across both the user and entity, will leverage the next
generation of data structures to deliver performance to increase breadth of supported security usecases with improved accuracy and scalability.
Correlation of security events across the environment is critical for timely detection of malicious behaviour and remediation. Correlation rules provide the logic to capture the tactics, techniques and procedures (TTP) employed by attackers across diverse platforms.
Proveho Networks SOC Management Services
Proveho Networks recognises different organisations
require different levels of SOC capability predicated on
acceptable risk limits and compliance requirements,
existing security baselines, internal capabilities, geofootprint
and vertical.
We have aligned with industry frameworks including NIST and MITRE ATT&CK, and partnered with leading security vendors to deliver tiered service level offerings to provide the flexibility required for security assurance across onpremise, data centre and cloud computing platforms.
Proveho leverages instrumentation to provide cohesion across computing domains and improve correlation capability, supplemented with external security intelligence to improve efficacy. The objective is timely identification and categorisation of anomalous and suspicious behaviour for further investigation and escalation, in order to manage risk and compliance.
Proveho Networks is committed to delivering the next generation automation and advanced analytics technologies as part of its SOC offering and extending the scope to include converging Cyber-physical (OT) and IoT domains.
Proveho’s SOC team leverages vendor supported and inhouse developed correlation rules to separate malicious activity from benign traffic across existing and emerging threats.
Proveho utilises automation and orchestration to improve efficiency with monotonous security tasks through standardised workflows and repeatable playbooks to manage increasing volume and velocity of threats, reduce investigation cycle times and apply an appropriate orchestrated incident response.



